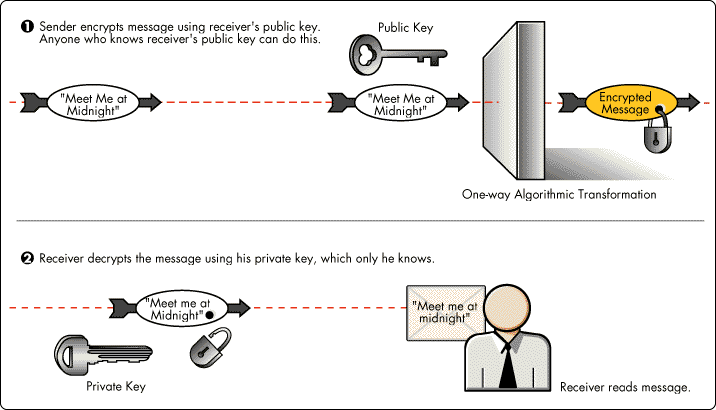
What is Public Key Encryption?

Public key encryption is based on cryptographic technology whereby two complementary keys—a key pair—are used to maintain secure communications. To send someone a private email message, you use a copy of that person’s public key to encrypt the information, which only they can decipher by using their private key. Conversely, when someone wants to send you encrypted mail, they use a copy of your public key to encrypt the data, which only you can decipher by using a copy of your private key. The key pairs are stored in key rings.
Encryption keys are based on encryption algorithms which ouput enciphered text or data. There are numerous encryption algorithms in the public domain, e.g. DES, RSA and Blowfish. These computer algorithms invariably produce keys with very large numbers and are all but impossible to 'crack' when used for encryption purposes.
The size of each key - public and private - is measured in bits; so, for example, you can have a1024-bit encryption key which will be very secure. Keys and key rings are stored as files on a computer hard drive. The files themselves are encrypted using the original, user defined, pass-phrase.
Creating and managing keys can be quite complex and so most people use an encryption 'front end' package that allows the encryption process to take place unattended. A popular, freeware, public key encryption package for the Windows operating system is PGP : Pretty Good Privacy. Owing to export restrictions in the USA - crytography is considered to be a type of military munitions - UK users should download what is known as the Internation version of PGP.
To create a private key the user is prompted to input a pass-phrase of xyz length. Generally speaking, the longer the pass-phrase the more sucure the encryption process. Once the pass-phrase is completed it is itself encrypted and stored as a file on the hardrive. Each time the pass-phrase is used to encrypt a piece of text/data it generates 'scrambled' output which is never again repeated (even when the same piece of text is encrypted again using exactly the same pass-phrase using exactly the same encryption software). Of course, in order to send someone an encrypted email they have to be able to decrypyt it themself. So how is the encryption security itself overcome when an authorised recipient wants to decrypt something? Well, each individual user's private pass-phrase produces a unique digital 'fingerprint'. This one-off digital 'fingerprint', conveyed to the recipient via a secure standard means of communication (e.g face to face or via the telephone), allows the recipient to be reasonably certain that all encrypted communications from this person are of the same source. This would include, for example, PGP signed email: the email itself may not need to be encrypted but the recipient may need to be certain that the sender is who they say they are and so a special 'signature' can be appended to a normal email to ensure this.
How can encryption remain secure if one part of the private-public pair is available to all and sundry (NB: there are even public key servers on the internet which allow people to find someone else's public key via their name or email address, for example)? This is a difficult concept to grasp until we remember that the public key is itself produced by the private key! The public key is of no practical use to anyone (for decryption purposes) if they do not have access to the private key which generated it or if they are not a trusted recipient of the unique digital 'fingerprint' mentioned above.
Public key encryption does, however, have its vulnerabilities. Leaving a pass-phrase on paper for someone else to read or using the same pass-phrase on a multi-user system. Also, tampering of a public key could leave a security gap that most people would not usually consider. There is also the possibility of someone actually 'cracking' the encryption itself, however, under normal circumstances this would take massive and inordinate computing power over an extended period of time (millions of years in some cases) and would hardly be worth the effort.
In passing, what does encypted text look like? Well, here is an example of the sentence "The cat jumped over the moon" encrypted using an RSA algorithm:
qANQR1DDBAQDAAHJL+3YV5joNgDCAYI2LxtFtHaYkiZ8zwzSA2IZQX8UJmqtAujjma8l3MZUKzw7wb/r=ab2h
Doesn't make much sense, eh! The only way of converting the above jargon back to something inteligible would be to de-crypt it using the public/private key 'ring' of an intended recipient or have the original creator decrypt it themself.